PPTP port: How PPTP Works
PPTP port belong to Point-to-Point Tunneling Protocol (PPTP). PPTP is a method for implementing virtual private networks that works on the data link layer. It serves the purpose of encrypting a remote computer’s network traffic to a host using Point-to-Point Protocol’s (PPP’s) authentication methods of PAP (Password Authentication Protocol) or CHAP (Challenge-Handshake Authentication Protocol). It was replaced by L2TP (Layer 2 Tunneling Protocol) or IPSEC (Internet Protocol Security) as a common remote network connection change, replacing dial-up network access to broadband access in recent years.
PPTP can be regarded as an extension of PPP, which provides router-to-router and host-to-network connections over asynchronous and synchronous connections. Since PPTP works on a data link layer (the second layer of a seven-layer model of network communications), it allows multi-protocol communications of the upper layers to be held using a secure communication channel over the Internet.
How does PPTP work?
According to Microsoft Corporation (2006) 1, the benefits of PPTP are:
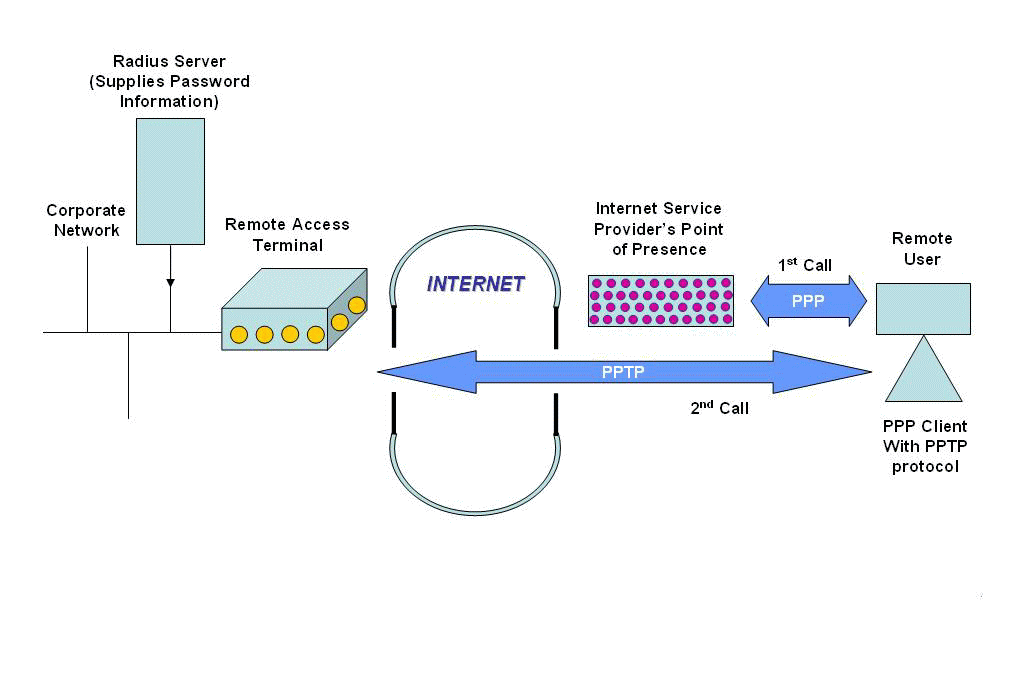
“Through PPTP, it is possible for remote users to access their corporate networks & applications by dialing into the ISP’s point of presence (POP), instead of dialing directly into the company network. PPTP connects directly to the target server by creating a virtual network for each remote client, one that the server administrator can monitor and manage like any other Remote Access port ”
The popularity of PPTP rests in the fact that it is the bundled dialup networking feature Microsoft put forth in most of its Windows Client products. (Microsoft was one of the members of the development group of PPTP).
RFC1334 defines both CHAP and PAP.
PAP according to RFC 1334 2:
The Password Authentication Protocol (PAP) provides a simple method for the peer to establish its identity using a 2-way handshake. This is done only upon initial link establishment.
After the Link Establishment phase is complete, an Id/Password pair is repeatedly sent by the peer to the authenticator until authentication is acknowledged or the connection is terminated.
PAP is not a strong authentication method. Passwords are sent over the circuit “in the clear”, and there is no protection from playback or repeated trial and error attacks. The peer is in control of the frequency and timing of the attempts.
Any implementations which include a stronger authentication method (such as CHAP, described below) MUST offer to negotiate that method prior to PAP.
CHAP according to RFC1334 2:
The Challenge-Handshake Authentication Protocol (CHAP) is used to periodically verify the identity of the peer using a 3-way handshake. This is done upon initial link establishment, and MAY be repeated anytime after the link has been established.
After the Link Establishment phase is complete, the authenticator sends a “challenge” message to the peer. The peer responds with a value calculated using a “one-way hash” function. The authenticator checks the response against its own calculation of the expected hash value. If the values match, the authentication is acknowledged; otherwise the connection SHOULD be terminated.
This authentication method depends upon a “secret” known only to the authenticator and that peer.
(Comment: Usually the secret refers to the peer’s password.)
The secret is not sent over the link.
(Comment: There is no way an attacker can gain access to the secret.)
This method is most likely used where the same secret is easily accessed from both ends of the link.
(Comment: On the authenticator’s side, we usually use a Radius server to store the password database centrally inside of it. (The Radius Server verifies the “secret” for the remote access terminal carrying out the authentication process with the peer.) The Challenge packet from the authenticator contains one octet of “Identifier” field and a variable stream of “Challenge” values. These two variables MUST be changed every time a Challenge packet is sent.)
The Response Value is the one-way hash calculated over a stream of octets consisting of the Identifier, followed by (concatenated with) the “secret”, followed by (concatenated with) the Challenge Value. The length of the Response Value depends upon the hash algorithm used (16 octets for MD5).
If the peer’s Response value matches what has been calculated by the authenticator using the same algorithm, then the authentication is successful.
References:
1 Microsoft Corporation (2006), How to Set Up a Windows NT PPTP Client, Available from: http://support.microsoft.com/kb/154062 [Accessed 28 March 2008]
2 Lloyd, B. Simson, W. (1992), Request for Comments: 1334, Network Working Group, Available from: http://rfc.net/rfc1334.html [Accessed 28 March 2008]

Leave a Reply